In today's world, where businesses and individuals alike rely heavily on the internet and digital technology, computer networks play a crucial role in facilitating communication and data transmission. From small home networks to large enterprise-level networks, these systems are the backbone of our connected world. In this blog, we will explore the basics of computer networks, how they work, and why they are so important.
What is Computer Networking?
Computer networking is the process of connecting multiple devices, such as computers, servers, routers, switches, and other devices, together to share resources and communicate with one another. Networks can be either wired or wireless and use a variety of protocols and technologies to enable devices to communicate and share data.
Networking enables devices to communicate with each other, share data, and access shared resources such as printers, files, and internet connectivity. It is essential for businesses, organizations, and individuals who need to share data, collaborate, and access resources remotely. Without networking, it would be difficult to share information and resources across multiple devices.
Types of Computer Networks
Computer networks can be methodically classified according to their scale or size, encapsulating a range of distinct types. Primarily, there are three prominent categories of computer networks.
LAN (Local Area Network)
A Local Area Network (LAN) is an interconnected group of computers that are strategically linked within a limited physical area, typically encompassing a building or office space.
The data is transferred at an extremely faster rate in Local Area Network.
The cost of building a LAN is less because of the inexpensive hardware used such as hubs, network adapters and ethernet cables.
A Local Area Network (LAN) offers enhanced security measures.
MAN (Metropolitan Area Network)
It is a network that covers a larger geographical area like cities by interconnecting LAN to form a larger network.
MANs employ a diverse range of wired and wireless technologies, including fiber optic cables and high-speed connections, to connect multiple locations within a metropolitan area.
MANs make use of various protocols such as RS-232, Frame Relay, ATM, ISDN, OC-3, ADSL, and more, to facilitate efficient communication and data transfer within the network.
MANs are designed to be scalable, allowing for the addition of new locations or the expansion of existing connections as the network requirements grow.
WAN (Wide Area Network)
It is a network that stretches across a large geographical area, connecting Local Area Networks (LANs) or Metropolitan Area Networks (MANs) together.
WANs leverage a mix of public and private telecommunications infrastructure, incorporating leased lines, satellite links, and service provider networks, to establish seamless connectivity among widely scattered locations.
WANs play an important role in connecting organizations to cloud services and data centers, enabling access to cloud-based applications, storage and computing resources.
WANs use public and private networks (leased lines, satellite links, etc.) to connect geographically distant locations.
Network Protocols
Network Protocol is a set of rules or algorithms that determine how data is transmitted between different devices in the same network. These protocols define how data is formatted, transmitted, received, and interpreted by different network devices.
Some different types of network protocols are listed below:
TCP/IP(Transmission Control Protocol/ Internet Protocol): The most widely used communication protocol that is used for transmitting data packets over the internet.
HTTP(Hypertext Transfer Protocol): It is an internet protocol that allows communication between a server and a browser.
DHCP (Dynamic Host Configuration Protocol): A protocol that automatically assigns IP addresses and network configuration settings to devices on a network.
FTP(File Transfer Protocol): A protocol that allows file sharing between servers by establishing two connections, one for data transfer(transfer of the actual files) and the other for control (controls information to ensure data retrieval in case of data loss).
SMTP (Simple Mail Transfer Protocol): The protocol used for sending email messages between mail servers.
IMAP (Internet Message Access Protocol): A protocol that allows email clients to access and manage email messages on a mail server.
POP3 (Post Office Protocol version 3): A protocol used for receiving email over the internet.
SSH(Secure Shell): It is a network protocol that enables computers to communicate and share data.
UDP(User Datagram Protocol): It is a connectionless transport protocol that lay-out a basic but unreliable message service. It operates at the transport layer of the TCP/IP protocol.
Telnet: It is a network protocol used for remote access to computers or devices over a network.
Network Topology
Now, let's talk about Network Topology.
Network Topology is a physical arrangement or structure of different devices connected together. It defines how devices are interconnected and how data flows within the network. The arrangement of a network comprises nodes and connecting lines via sender and receiver.
Here are some commonly used network topologies and their limitations are as follows:
Bus Topology
It is a network topology in which every computer and network device is connected to a common cable or backbone. Data is transferred along the backbone, and each device listens for its specific data.
Limitations:
As the network expands, the scalability of bus topology diminishes, and the performance of the network is affected when new devices are added, primarily due to the shared communication channel among all devices.
Bus topology relies on a single backbone or cable to connect all devices, making them vulnerable to network disruptions if the backbone cable fails.
Ring Topology
In a ring topology, devices are interconnected in a circular loop, with each device being connected to its adjacent devices. Data is transmitted in a unidirectional manner, flowing continuously around the ring.
Limitations:
If one of the cables breaks, the entire network fails and there will be no transferring of data.
A lot of unnecessary calls are made. For example, if we want to transfer data from A to D, we have to send data through B and C before reaching D.
Star Topology
In a star topology, all devices are connected to a central hub or switch, which serves as the central controlling device. Data is transmitted through the hub, and communication between the devices is facilitated by the hub.
Limitations:
In star topology, each device is dependent on the central hub or switch, and if the hub fails the entire network falls.
The implementation cost of a star topology is higher compared to other topologies due to the additional requirements of extra cabling and a central hub or switch, resulting in increased overall expenses.
Tree Topology
It is a connection of multiple star topologies interconnected through a central device. It is also known as hierarchical topology. It resembles a tree structure with branches and sub-branches.
Limitations:
As the network expands more branches are added and the complexity of the network increases making it difficult to troubleshoot.
The cost of implementing and maintaining the tree topology is much higher as compared to other topologies.
Mesh Topology
In a mesh topology, each device is connected to every other device in the network making a mesh-like structure.
Limitations:
Scaling a mesh topology can become challenging as the number of devices increases. The number of required connections grows exponentially, making it difficult to manage and maintain as the network expands.
Mesh topologies can be complex to design, implement, and manage. The number of interconnections required between devices increases significantly as the network size grows.
OSI Model
The OSI (Open Systems Interconnection) model serves as a conceptual framework for describing the communication process between two systems within a network. It establishes a set of seven distinct layers, each with its own defined tasks and responsibilities. By providing a standardized approach to network communication, the OSI model enables interoperability and seamless interaction between different systems and technologies. This protocol was meant to be a protocol suite for power networks but was lost to TCP/IP.
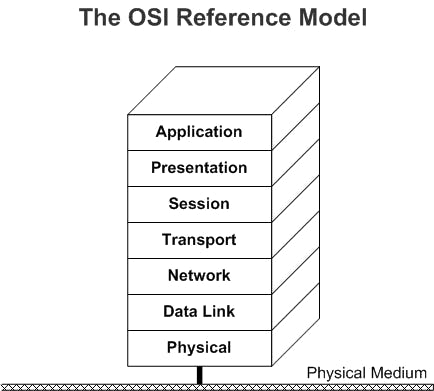
Let's take an overview of the seven layers of OSI models, which are as follows:
Application Layer: The Application layer is the top layer of the OSI Model and is the one on which the end user interacts every day. This layer is not where actual applications live, but it provides the interface for applications that use it like a web browser. It includes protocols for email, file transfer, web browsing, and other application-specific functionalities. Examples of application layer that we use daily are HTTP, DNS, SSH and DNS.
Presentation Layer: The presentation layer is responsible for the formatting and representation of data by translating between application and network formats. This layer allows two systems to use a different encoding for data and still pass data between them. It also handles data encryption, compression, and character encoding.
Session Layer: The session layer establishes, manages, and terminates communication sessions between applications. It builds, manages, and terminates the connection between local and remote applications.
Transport Layer: This layer transfers data between applications, providing reliable data transfer services to the upper layers. The transport layer controls a given connection's reliability through flow control, segmentation and designation, and error control. This layer tracks the segments and retransmits those that fail. TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) operate at this layer.
Network Layer: The network layer focuses on the routing and forwarding of data packets across multiple networks. It determines the optimal path for data transmission and handles logical addressing and routing protocols. Routers also operate at this layer, sending data throughout the neighboring networks.
Data Link Layer: This layer is responsible for the host-to-host transfers on the same network. It defines the protocols to create and terminate the connection between the two devices. Ethernet switches and network interface cards (NICs) operate at this layer.
Physical Layer: Physical layer is responsible for the transmission and reception of raw unstructured data bits over a physical medium, such as cables, wires, or wireless signals. This layer converts data in the form of digital bits into electrical, radio, or optic signals.
The OSI model serves as a reference framework for network designers, developers, and vendors, allowing them to understand and implement network protocols and technologies that adhere to the same layered structure.
TCP/IP Model
The TCP/IP (Transmission Control Protocol/Internet Protocol) model serves as a fundamental framework that describes the protocols and communication processes essential for the operation of the Internet and various computer networks.
Unlike the seven-layer OSI model, the TCP/IP model consists of four layers that govern the protocols and communication processes within computer networks and the Internet.
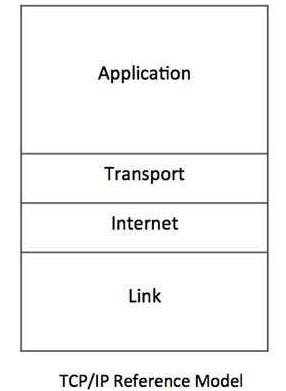
Note: The layer count in the TCP/IP model is occasionally described as either four or five layers, depending on the perspective or interpretation. The Physical Layer and Data Link Layer are referred to as one single layer.
We'll talk only about 4 layers with specific functions and protocols:
Network Interface Layer: This layer is also known as the Link Layer. It focuses on the physical transmission of data within the network. It encompasses networking protocols that are specific to the local network to which a host is connected. This layer involves protocols for accessing the network medium, like Ethernet or Wi-Fi, and handles device addressing within the local network.
Network/Internet Layer: This layer is responsible for transmitting data between networks. It uses IP (Internet Protocol) to assign unique IP addresses to devices, enables packet forwarding, and determines the optimal path for data transmission.
Transport Layer: The Transport Layer ensures reliable and orderly data delivery between the devices. TCP and UDP are the primary protocols of this layer that provide host-to-host communication services for applications. Transport protocols are responsible for connection-oriented communication, reliability, flow control, and multiplexing.
Application Layer: The Application Layer serves as the interface between applications and the network, facilitating communication between them. In the TCP/IP model, this layer encompasses the communication protocols utilized for process-to-process interactions across an IP network. It encompasses protocols like HTTP for web browsing, SMTP for email communication, and a variety of others.
The TCP/IP model is the Internet's foundation, enabling standardized network communication, and interoperability between devices, operating systems, and applications. It is commonly compared to the OSI model, with TCP/IP's Internet Layer aligning with OSI's Network Layer and its Transport and Application Layers encompassing multiple OSI layers.
Client-Server Architecture
Client-server architecture is a computing model in which the server hosts, delivers and manages most of the resources and services to be consumed by the client. This type of architecture has one or more client computers connected to a central server over a network or internet connection.
Client devices, such as personal computers or smartphones, initiate communication by sending requests to the server, relying on its capabilities and resources to meet their requirements. The server, whether a dedicated computer or a cluster of computers, processes these requests and delivers the requested services or data to the clients.
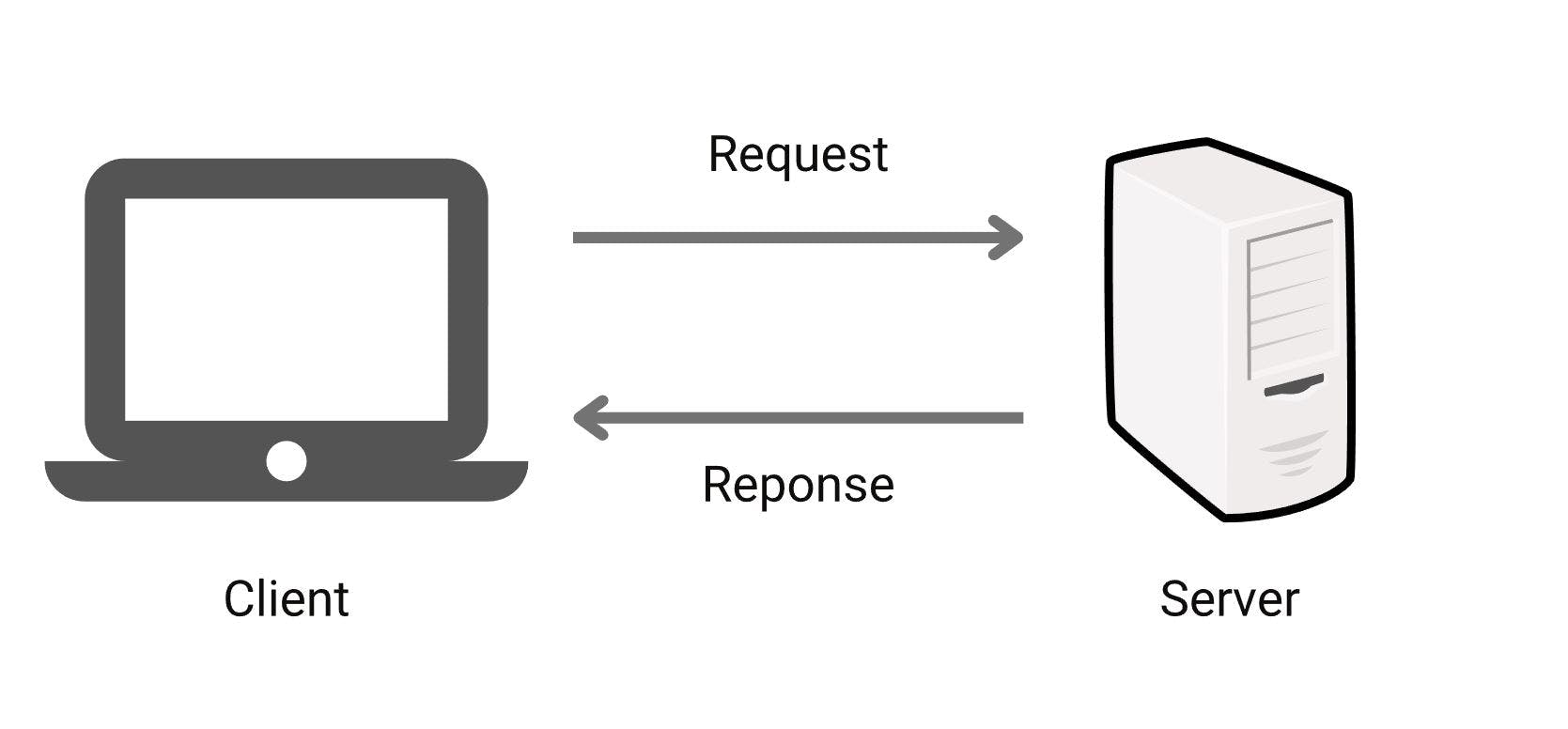
The client-server architecture provides numerous benefits. It facilitates centralized resource management and control, with the server holding and managing data and services. Scalability is achieved as the system can handle an increasing number of clients without compromising performance. Furthermore, specialization is enabled, allowing servers to be optimized for specific tasks or services, while clients focus on user interaction and interface.
Common examples of client-server architecture include web browsing, where a client (web browser) sends requests to a server (webserver) to retrieve and display web pages, and email communication, where a client (email client) connects to a server (email server) to send and receive emails.
Peer-to-peer Architecture
Peer-to-peer (P2P) architecture is a network model in which all devices, known as peers, have equal privileges and can act as both clients and servers. P2P networks distribute the workload between peers, and all peers contribute and consume resources within the network without the need for a centralized server.
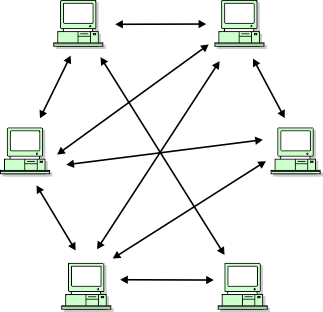
In a peer-to-peer network, each device can initiate and respond to requests, as well as share its own resources, such as files, processing power, or network bandwidth, with other peers. This distributed approach enables efficient resource utilization and can provide increased fault tolerance as there is no single point of failure.
Peer-to-peer (P2P) architecture presents multiple advantages. It enables seamless sharing and collaboration, as peers can directly exchange data and resources without intermediaries. Additionally, P2P architecture offers scalability by allowing the network to accommodate more peers without compromising its overall performance.
Prominent instances of peer-to-peer architecture encompass widely-used applications such as BitTorrent, where peers directly share files, and cryptocurrency networks like Bitcoin, where peers autonomously validate and transmit transactions without relying on a central authority.
Conclusion
In conclusion, computer networks have revolutionized our connectivity and communication, serving as a vital cornerstone in our modern digital world. Throughout this exploration, we have delved into the multifaceted aspects of computer networking, encompassing crucial topics such as network types, protocols, topologies, and architectural models. By understanding and harnessing these fundamental elements, we unlock the power to create robust, efficient, and secure networks that underpin our technological landscape.
Feel free to connect with me on Twitter and LinkedIn to stay updated with the latest insights and discussions on computer networking!

